From raw crime databases to comprehensive intelligence reports—this series has demonstrated a complete technical pathway for transforming criminal network analysis from manual investigation into automated, AI-powered intelligence generation.
We began with millions of administrative records from the Chicago Police Department and progressively built a system that not only identifies criminal organisations with mathematical precision but also generates comprehensive intelligence reports that provide crucial insights for investigative decision-making. The journey encompassed three critical phases: extracting meaningful relationships from raw data through knowledge graph construction (article 1), applying graph data science algorithms to reveal criminal group structures and hierarchies (article 2), and deploying specialised AI agents to synthesise network insights into professional intelligence products (article 3).
Beyond graph analysis: Reasoning and pattern detection in criminal network analysis
The final system delivers more than summaries of graph analysis results. Through systematic prompt engineering and coordinated AI agents, the intelligence reports provide sophisticated reasoning capabilities that detect operational patterns and identify intervention opportunities based on network structure, temporal behaviours, and geographic patterns.
These insights support critical investigative decisions: which individuals to target for maximum network disruption, when and where to deploy surveillance resources, and how criminal organisations adapt their operations over time.
Implementation study insights
This fourth and final post synthesises the lessons learned from our complete implementation study, providing practical guidance for organisations embarking on similar AI-powered analytical systems. Rather than focusing on specific technical details covered in previous posts, we examine the broader challenges encountered when deploying these technologies at scale, the unexpected insights that emerged from working with real operational data, and the critical decisions that determine whether such systems produce meaningful intelligence reports or merely academic exercises.
What you’ll find here
We distil the key insights about data transformation challenges, the essential role of graph data science in revealing hidden patterns, how agentic AI architectures enable reliable analysis automation, and why systematic evaluation proves crucial for operational deployment. We also outline the future development directions that emerged from this work—specialised models, autonomous analysis capabilities, and interactive intelligence systems that could transform how law enforcement approaches criminal investigation.
The lessons covered here apply beyond criminal intelligence to any domain requiring systematic analysis of complex relational data followed by professional intelligence generation. Understanding these implementation insights helps ensure your system produces operationally viable results that support critical decision-making rather than experimental prototypes.
Data processing and transformation
The implementation reveals critical insights about transforming raw law enforcement data into actionable intelligence. Raw crime and arrest databases contain millions of records in formats designed for administrative processing, not analytical insight. The key breakthrough involves systematic data reduction through network projection—transforming bi-partite crime-offender relationships into focused co-offending networks that reveal criminal collaboration patterns invisible in original tabular formats.
This process reduces the analysis scope from millions of individual records to manageable criminal group datasets containing dozens of members and hundreds of relationships. The transformation makes comprehensive analysis computationally feasible while concentrating investigative focus on organised criminal activity rather than isolated incidents. This approach applies beyond criminal network analysis to any domain requiring pattern detection in large relational datasets.
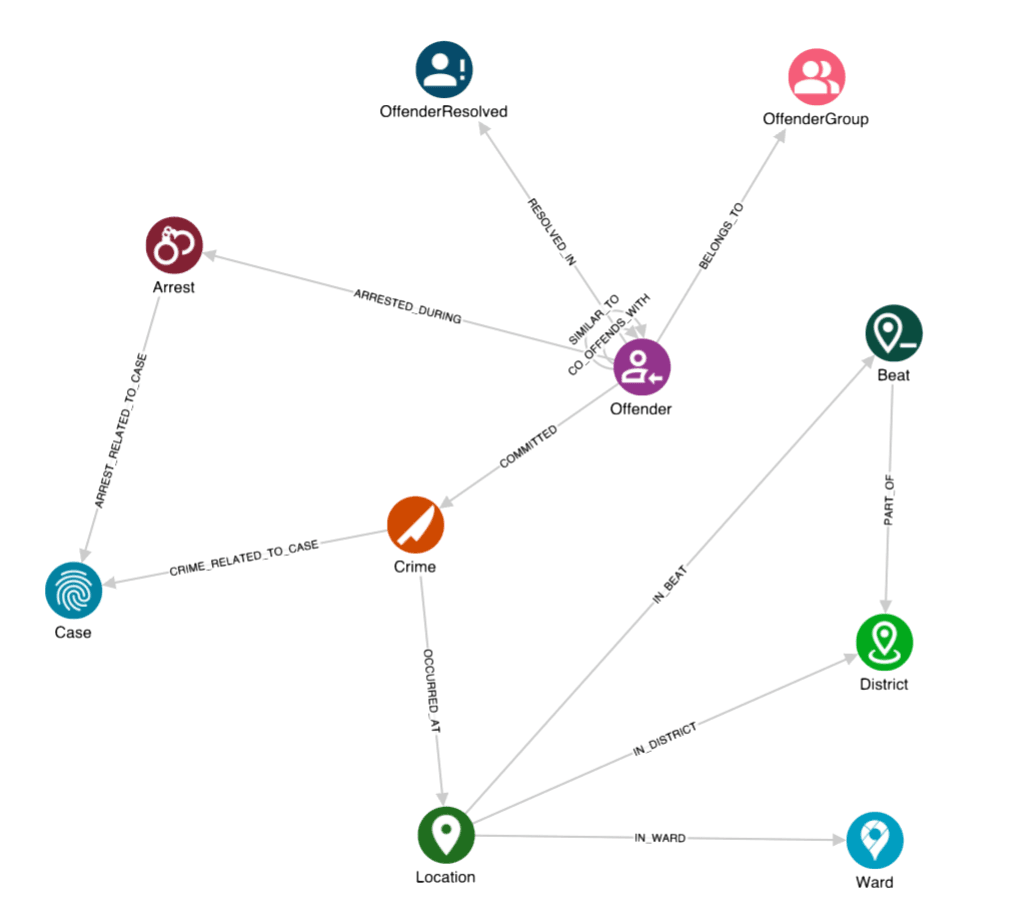
Graph data science as an analytical foundation
Graph data science algorithms prove essential for extracting meaningful intelligence from criminal relationship data. Community detection algorithms like Louvain automatically identify criminal group boundaries that would require weeks of manual investigation to establish. Network centrality measures—PageRank and betweenness centrality—reveal operational hierarchies and communication brokers that traditional database queries cannot detect so easily.
The progression from whole-network analysis to subnetwork focus demonstrates how graph algorithms scale across different analytical granularities. Initial analysis of the complete criminal network identifies organised groups, then detailed subnetwork analysis reveals internal structure and individual roles. This multi-scale approach enables both strategic intelligence about criminal ecosystems and tactical intelligence about specific organisations.
LangGraph for reliable agentic workflows
LangGraph architecture addresses the fundamental challenge of ensuring consistent, explainable results from AI-powered analysis systems. Parallel agent processing with defined state management eliminates the randomness and contradictory outputs that plague single-model approaches. Each agent operates independently on the same structured input, performs defined analytical tasks, and produces formatted HTML output that integrates seamlessly into the final intelligence report.
This parallel approach offers significant technical advantages over sequential processing. Each agent operates independently on the same input data, eliminating the need to pass long sequences of intermediate tokens between agents that would consume substantial context windows. Rather than agents producing different intermediate formats requiring subsequent transformation, each agent outputs directly to structured HTML, reducing both processing complexity and token consumption while dramatically reducing total processing time.
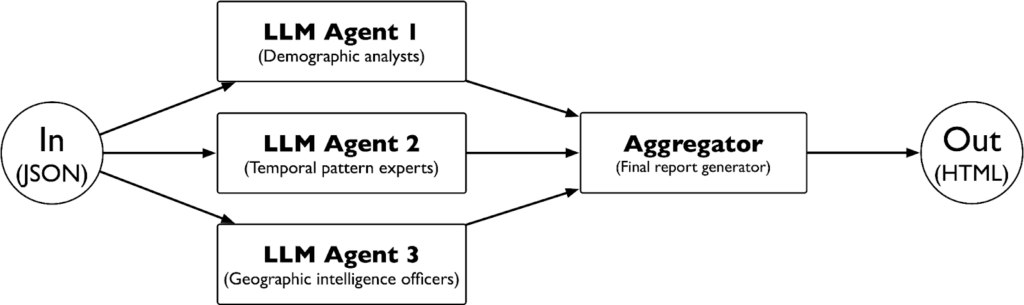
The workflow design ensures reproducible results across different criminal groups while maintaining analytical depth and isolation between analytical domains. Specialised agents consistently apply domain expertise—demographic analysis, temporal pattern recognition, geographic intelligence—without the analytical drift that occurs when general-purpose models attempt comprehensive analysis or when sequential processing creates dependencies between analytical phases. If one agent encounters processing difficulties, the other analytical domains remain unaffected, preventing cascading errors that could compromise the entire analysis.
This architecture enables reliable automation of complex analytical processes previously requiring manual coordination between multiple human specialists, while optimising both speed and resource efficiency through parallel execution and direct output formatting.
Systematic prompt engineering and evaluation
The development process demonstrates how systematic prompt engineering and evaluation transform generic AI output into professional intelligence products. Role-based prompting, structured output formatting, and constraint specification collectively ensure agents produce analyses appropriate for law enforcement decision-making rather than academic discussion.
The LLMs-as-judge evaluation methodology provides a scalable quality assessment that enables iterative improvement across large datasets. Randomised comparison testing with bias mitigation techniques offers objective measurement of prompt engineering effectiveness. This evaluation approach enables continuous system improvement without requiring extensive manual assessment by domain experts.
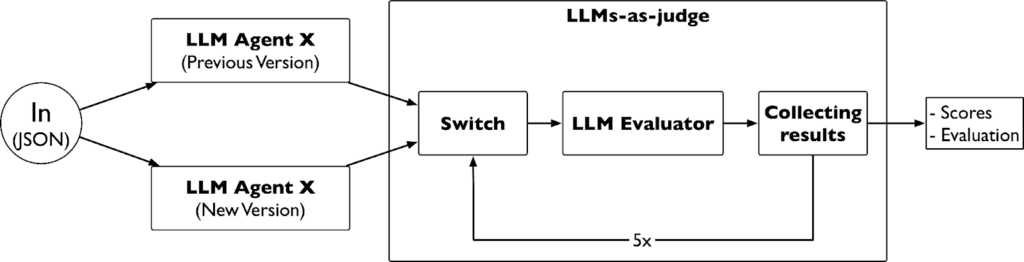
Broader applications and transferable methods
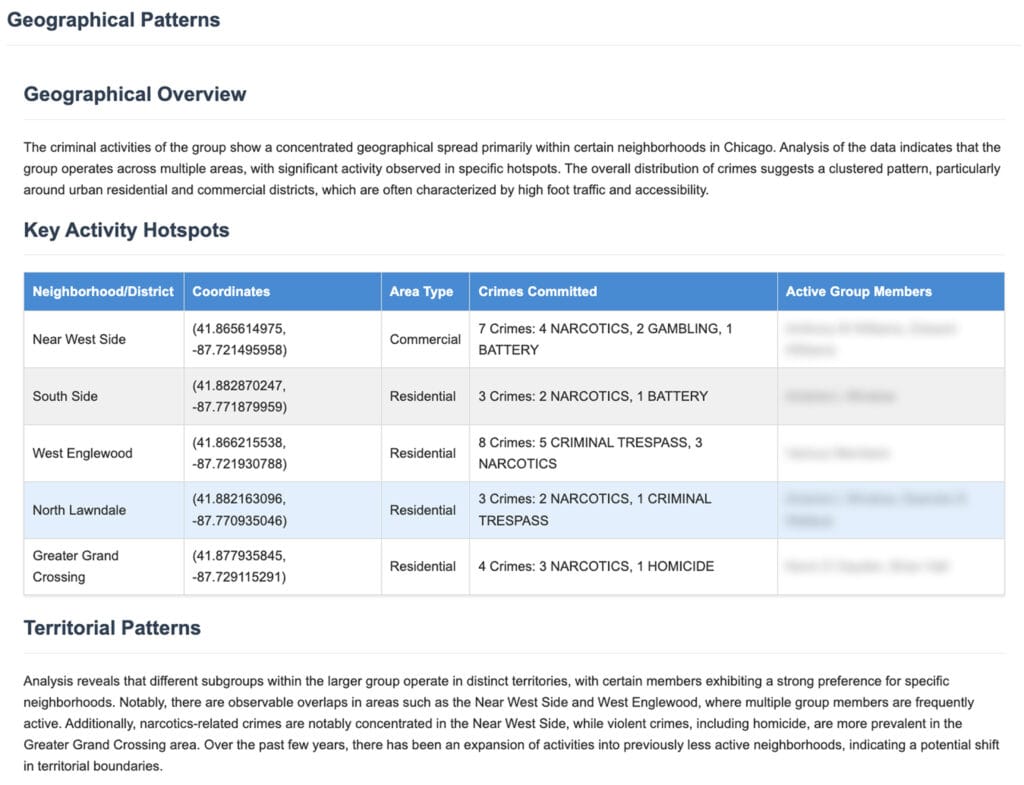
These technical approaches extend far beyond criminal network analysis to address diverse law enforcement intelligence challenges. Geographic risk assessment can apply similar graph-based clustering to identify high-crime areas and underlying factors. Temporal crime analysis can use specialised agents to examine seasonal patterns, escalation trends, and operational timing across different crime types. Resource allocation decisions can leverage agent-based analysis to optimise patrol deployment and investigative prioritisation.
The combination of graph data science for pattern detection, agentic workflows for reliable processing, and systematic evaluation for quality assurance creates a generalisable framework for transforming complex law enforcement data into actionable intelligence.
Future development directions
This was our first implementation study, from which we gained valuable insights to build on. Here are the future developments we’ve identified.
- Specialised language models: Rather than deploying general-purpose large language models, future systems can utilise specialised models optimised for specific analytical tasks. Focused models for group composition analysis, temporal pattern recognition, and geographic intelligence can operate on standard hardware while delivering superior domain-specific performance. Experienced analysts play crucial roles in creating training datasets that capture nuanced domain knowledge and analytical best practices.
- Autonomous information retrieval: Advanced systems can integrate tools and Model Context Protocol (MCP) capabilities that enable autonomous data access and analysis path determination. Rather than processing predetermined data, systems can dynamically query knowledge graphs, extract relevant information, and adapt analytical approaches based on emerging patterns. This capability extends analysis beyond anticipated questions to address novel investigative requirements.
- Interactive intelligence systems: The ultimate evolution moves beyond static report generation toward question-answering interfaces that enable flexible analytical interaction. Analysts can pose specific investigative questions, and systems evaluate optimal analytical pathways, deploy appropriate specialised agents, and provide explainable reasoning supporting conclusions. This approach transforms AI systems from report generators into interactive intelligence partners that adapt to evolving investigative needs while maintaining the explainability standards required for law enforcement applications.
These developments collectively enable more responsive, specialised, and interactive intelligence systems that scale analytical capabilities beyond current human-AI collaboration limitations.
Production applicability and real-world considerations
This implementation study demonstrates the significant value and effectiveness of combining knowledge graphs with AI agents for criminal intelligence analysis. The results—identifying criminal leaders, generating comprehensive reports in hours rather than weeks, and revealing patterns invisible to manual analysis—clearly justify pursuing production deployment. However, transitioning from implementation study to operational systems requires addressing several critical considerations that extend beyond the technical architecture described in this series.
We deliberately introduced certain constraint relaxations during this study to focus on demonstrating the complete end-to-end process and validating the core technical approach. The specific security, privacy, and operational concerns discussed below vary significantly across organisations, jurisdictions, and regulatory environments, making them more suitable for private consultation rather than generic guidance.
Data security and privacy: The primary challenge
The most significant consideration for production deployment involves data security and privacy requirements. Our implementation study utilised publicly available Chicago Police Department data, which allowed us to focus on technical development without navigating complex data handling restrictions. However, operational law enforcement data contains highly sensitive information—personal identifiers, detailed crime descriptions, investigative methods, and ongoing case details—that cannot be shared with external cloud providers under standard terms of service.
While major AI providers clearly state they won’t use customer data for model training purposes, very few explicitly guarantee that data won’t be logged or retained for operational purposes. This logging concern becomes critical when processing data containing names, addresses, crime details, and other sensitive law enforcement information. Organisations considering production deployment must carefully evaluate their data handling requirements against provider terms of service and regulatory compliance obligations.
Mitigation strategies under investigation
Several approaches can address these security concerns, each with distinct trade-offs requiring careful evaluation:
Local LLM deployment: Organisations can deploy open-source language models within their own infrastructure, ensuring complete data control and eliminating external data sharing. Our preliminary experiments in this direction reveal important considerations: current open-source models deliver noticeably lower analysis quality compared to leading cloud providers, while the infrastructure costs and maintenance requirements for hosting capable local models can exceed cloud service expenses. However, this landscape evolves rapidly as open-source model capabilities improve and deployment tools mature.
Data anonymisation: Systematic anonymisation can remove sensitive identifiers while preserving analytical utility. Personal names can be replaced with consistent pseudonyms without affecting network analysis or intelligence generation—whether an offender appears as “Alessandro” or “Christophe” has no impact on relationship detection or role identification. However, anonymisation becomes more complex with crime details and operational methods, where specific information about weapons, techniques, or locations may be essential for pattern recognition and intelligence quality.
Government LLM infrastructure: Many countries are developing dedicated AI infrastructure for government use cases, providing law enforcement organisations with AI capabilities that maintain data within national boundaries and comply with sensitive data handling requirements. These emerging solutions could provide the analytical power of advanced language models while meeting the security standards required for operational law enforcement data.
Human-in-the-loop integration challenges
Beyond security considerations, many organisations require greater human oversight and control over generated intelligence reports. While this oversight provides important quality assurance and accountability, it introduces operational challenges that must be carefully managed. Human review of every generated report can significantly slow down the analysis process, potentially negating the speed advantages that justify AI deployment.
Effective human-in-the-loop integration requires personnel with a deep understanding of both the underlying analytical methods and the AI system’s capabilities and limitations. This expertise requirement, combined with the need for specialised interfaces that most platforms don’t provide out-of-the-box, can create implementation barriers that require custom development and specialised training programs.
Strategic recommendations for production transition
The implementation study clearly demonstrates that the analytical value and operational benefits justify addressing these production considerations. However, the security, privacy, and operational considerations discussed above are not generic challenges with universal solutions. Each organisation faces unique regulatory requirements, security constraints, infrastructure capabilities, and operational preferences that demand customised mitigation strategies.
Our recommendation for organisations interested in production deployment is to engage in detailed consultation to develop organisation-specific implementation plans. These discussions should address your particular security requirements, evaluate mitigation strategies appropriate for your regulatory environment, assess the trade-offs between different deployment approaches, and design human oversight integration that maintains analytical efficiency while meeting accountability standards.
The concerns outlined above represent important considerations for production deployment, not insurmountable barriers. The demonstrated value of AI-powered criminal intelligence analysis—more accurate, faster, and more comprehensive than manual approaches—clearly justifies the effort required to address these implementation challenges through proper planning and customised solutions.
‘Combining knowledge graphs and LLMs can speed up criminal network analysis’ series
This article is part of a series exploring how combining knowledge graphs and LLMs can speed up criminal network analysis:
- Article 1: Extracting meaningful relationships from raw data through knowledge graph construction
- Article 2: Applying graph data science algorithms to reveal criminal group structures and hierarchies
- Article 3: Deploying specialised AI agents to synthesise network insights into professional intelligence products
- Article 4: Lessons learned and next steps for advancing this approach
Knowledge graphs and LLMs in action
If you would like to read more about techniques that combine knowledge graphs and LLMs, read our book from Manning.
Book preview
To know more about GraphAware Hume, the graph-powered intelligence platform we used for our study, visit our website: graphaware.com

