The GraphAware team is excited to release the neo4j-sso third-party security extension, compatible with Neo4j Enterprise, version 4.0 and above.
It allows Neo4j Enterprise users to connect with their LDAP, Okta, Google or Azure Active Directory (and many other providers) accounts in a seamless and secure way.
It has many benefits from a security perspective, where the two most prominent are:
repudiation: It removes most of the need for service accounts where more than one user would use the same set of credentials for connecting to Neo4j, thus tracing every action against a Neo4j server back to a single individualmisconfiguration and availability: If you ever had to configure Neo4j to federate LDAP, you would know that the configuration is a tedious process, can easily be misconfigured and more importantly, it requires you to restart all the nodes of your Neo4j cluster, which has a serious impact on production applications
What is Single Sign-On?
Single Sign-On is an authentication scheme that allows users to log in with a single ID to any of several related, yet independent, software systems.
What is Keycloak?
Keycloak is an open-source Identity and Access Management solution aimed at modern applications and services. It makes it easy to secure applications and services with little to no code.
How does it work?
TLDR;
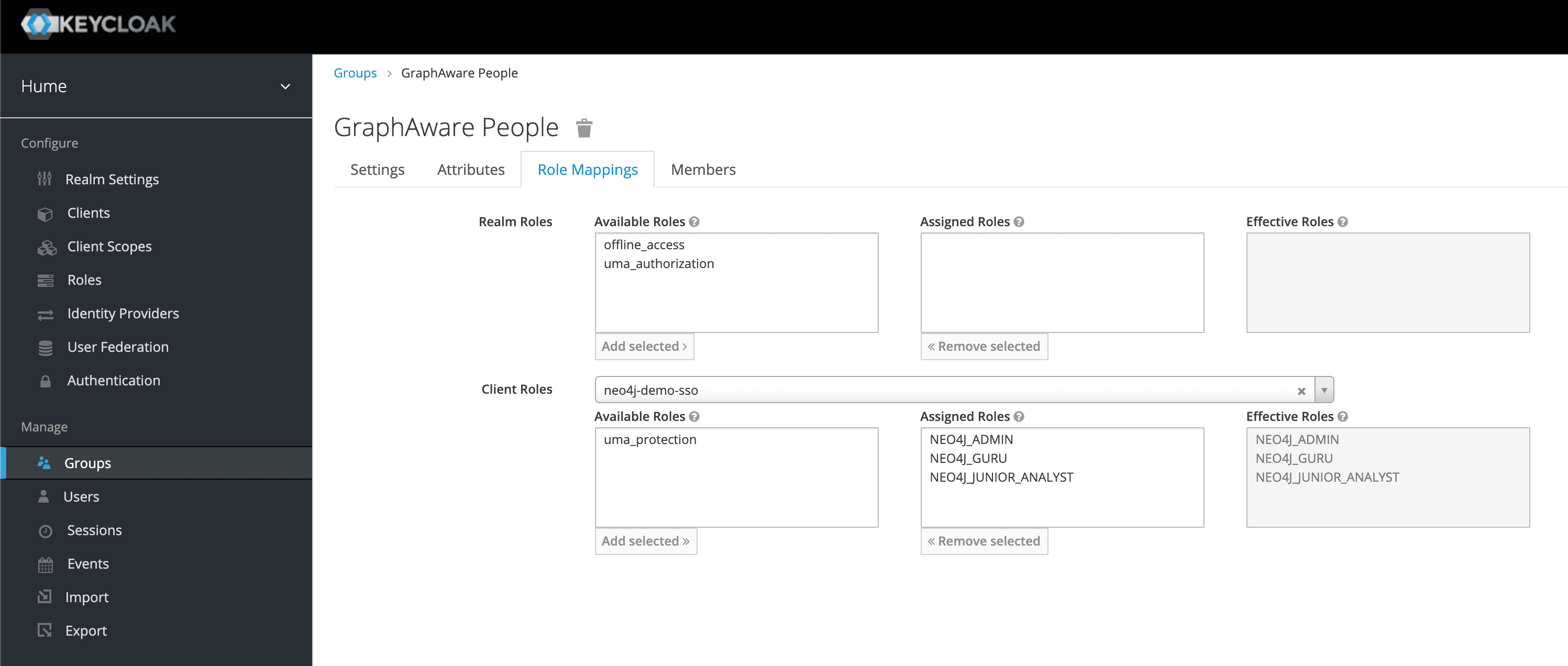
In Neo4j, leveraging the RBAC system, you will configure roles and which permissions those roles have on the graphs.
In Keycloak, you will configure where your users come from (using identity providers or Federation) and which information from their identity has to be used in order to determine which roles they will be mapped to when connecting to Neo4j.
Traditional login with credentials
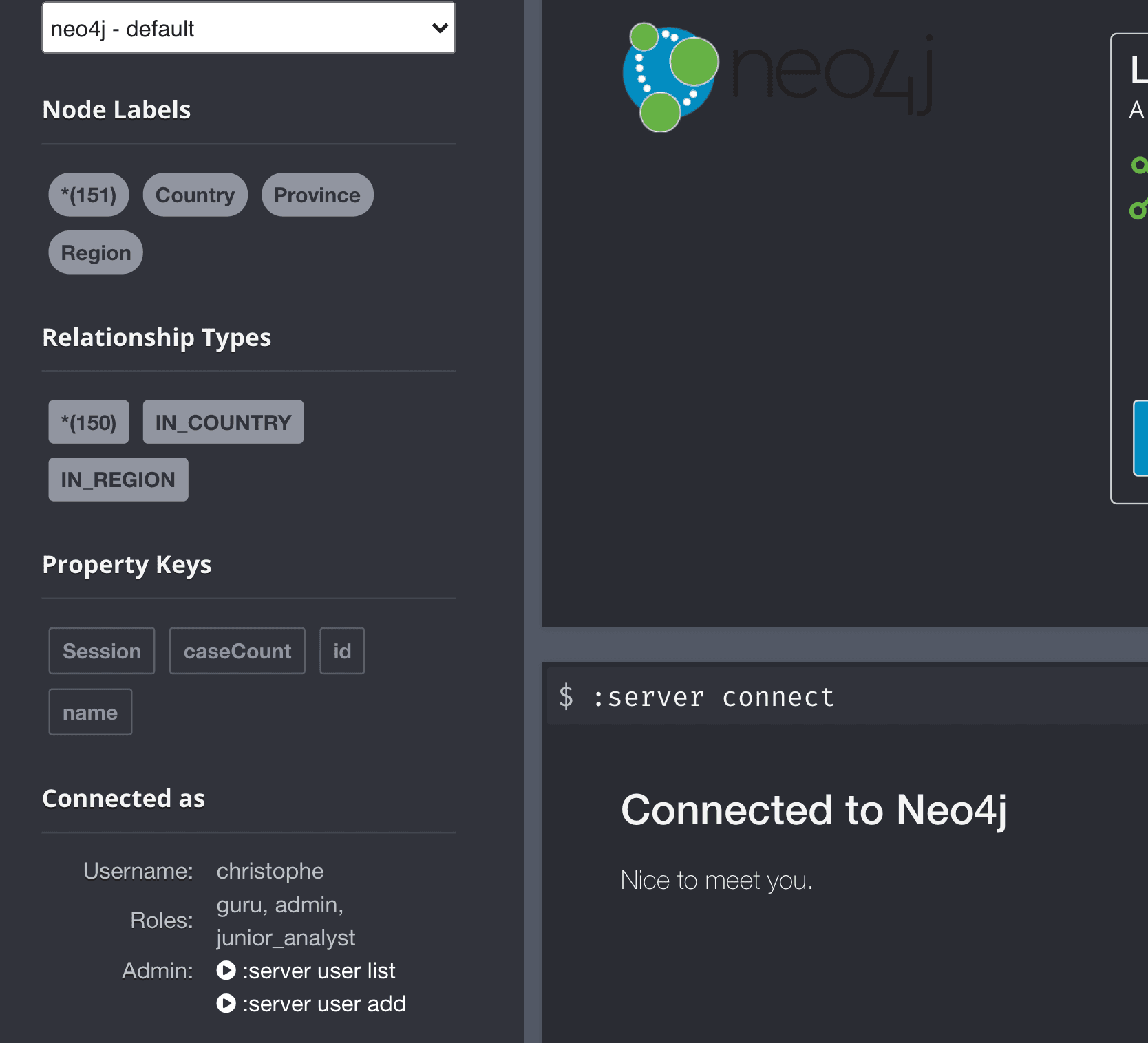
If you connect via the Neo4j browser, you can use your identity provider credentials. The SSO extension will proxy the authentication to Keycloak.
In turn, Keycloak, being configured to map the identity information from the original provider correctly to Neo4j’s specific roles, will return a new identity to the SSO extension that will authenticate and populate the user information in the Neo4j server.
OpenID login with token
Credentials are not the only way to connect. In fact, Keycloak produces an OpenID-compliant token which can be used to connect to Neo4j via the browser, but most importantly from applications as well.
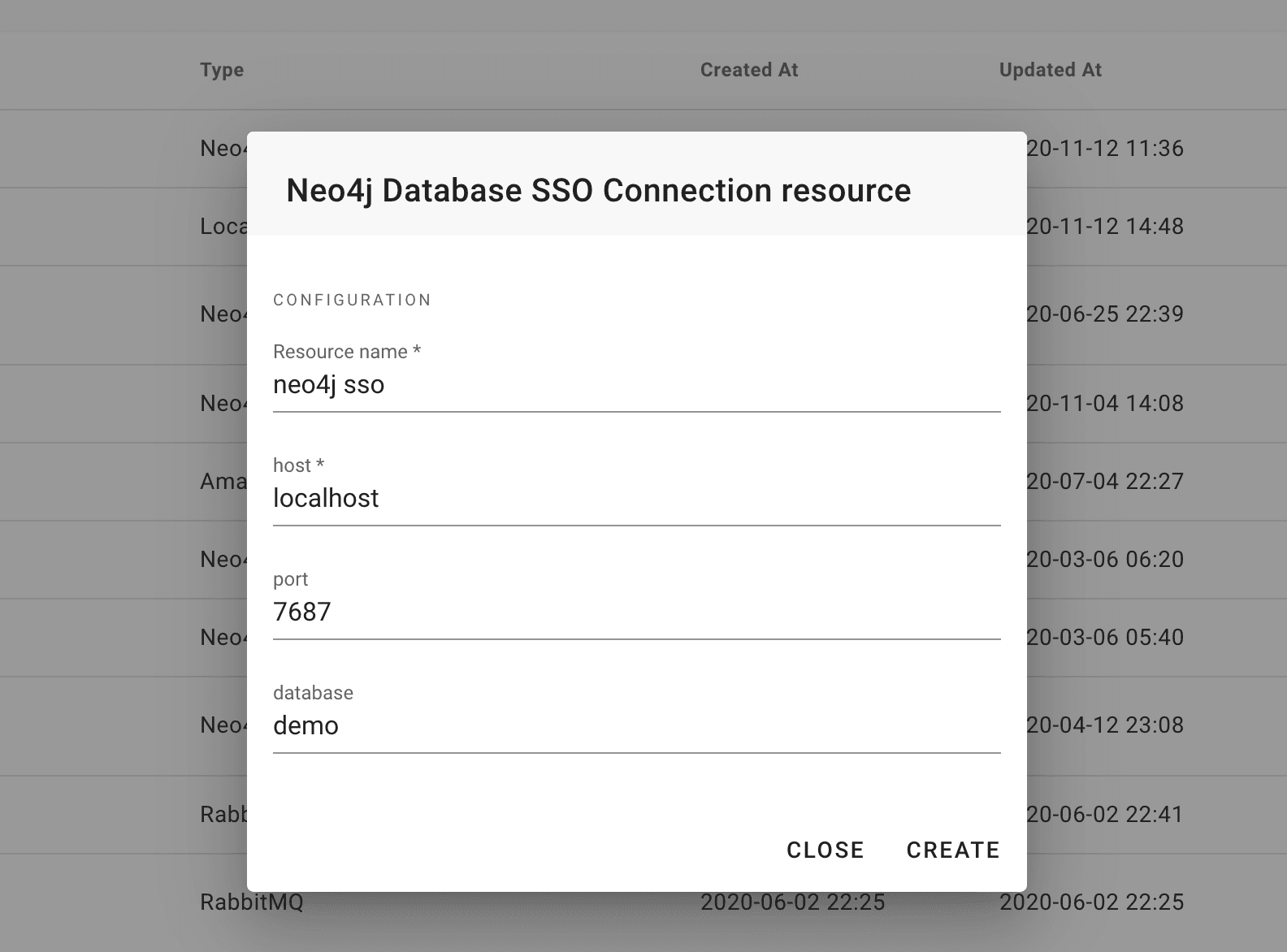
GraphAware Hume, our Graph-Powered Insights Engine, leverages this new authentication mechanism.
Hume users connect once via SSO, and do not have to enter any credentials for how to connect to Neo4j. Configuring Neo4j connections from the Hume ecosystem is now as simple as this
Summary
Single Sign-On increases the security of your Neo4j server as well as applications connecting to it. SSO is also a required security control in the FedRAMP compliance program, for which our GraphAware Hume product has been assessed.
Want to know more?
Contact us via the contact page on the website, or drop us an email at info@graphaware.com. A GraphAware representative will get in touch with you.

